
Cybersecurity is a rapidly advancing field and every day you hear about new developments, threats, and technologies. There’s a thrill to keeping your finger on the pulse and constantly learning about those major stories that steal the headlines. Because after all, if you’re in the Security Operations Center (SOC), that’s your job, right?
But when does the noise quite down, and real opportunities present themselves? You can drive yourself crazy trying to keep up with all the news articles, tweets, and major security vendors trying to convince you of the biggest threats facing your business today. There’s a harmful incentive to a “fear-monger” approach and as a result, it’s difficult to tell what’s worth paying attention to. You feel the pressure to declare that you’ve protected against every single threat that comes down the pipe, awkwardly answering ‘We’re safe.’
In most cases, the news cycle moves on and those threats fade away into obscurity. All that scrambling to get the newest and greatest technology turns into sunk costs. The cycle then repeats again, and again. You end up on a hamster wheel where you feel like you’re making progress, but all you’re actually doing is burning through your budget.
“It does not make sense for the Security Operations Center to prioritize new technology when the existing assets are effective”
Instead, what you should focus on is a baseline measurement of the people, processes, and technology that you’ve already got in place that reduces the risk posed by the latest and greatest threat. If you’ve already got a strong and mature access and identity management program in place – then don’t look to optimize regardless of market trends. It does not make sense for the Security Operations Center to prioritize new technology when the existing assets are effective. Even if you’re brand new to building a cybersecurity program, you’ll find that your I.T. professionals have already implemented some cybersecurity controls.
Before you take on any new cybersecurity components into your technology stack, make sure you have a nuanced and comprehensive understanding of how your current assets are performing and how they could be made more effective.
To better understand how to think about this, let’s look at how to think about measuring your existing cybersecurity investments:
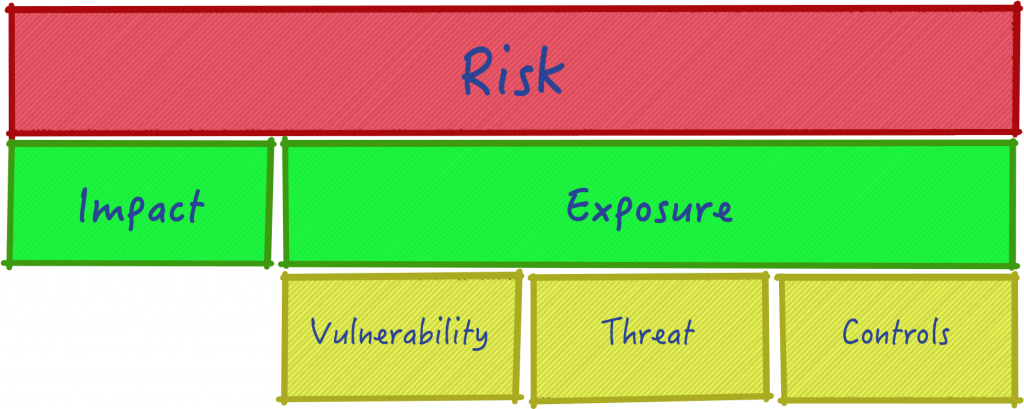
What you’re trying to mitigate here, at its essence, is risk. A risk is defined as the possibility of harm that can come to an asset or organization. This is split into two different types, namely: inherent risk which is the level taken on by owning a technology, asset or doing a task; and then residual risk which is the risk left over after all controls have been applied to minimize the impact, likelihood, or vulnerable state.
When risk is managed correctly and a weakness or vulnerability is exploited, the negative results is referred to as the impact. The objective of your cybersecurity program is to minimize the impact by putting in place a wide range of controls. Controls are referred to as measures put in place to increase the protection for an asset, to make up for a lack of protection for an asset, or to strengthen a weakness for an asset.
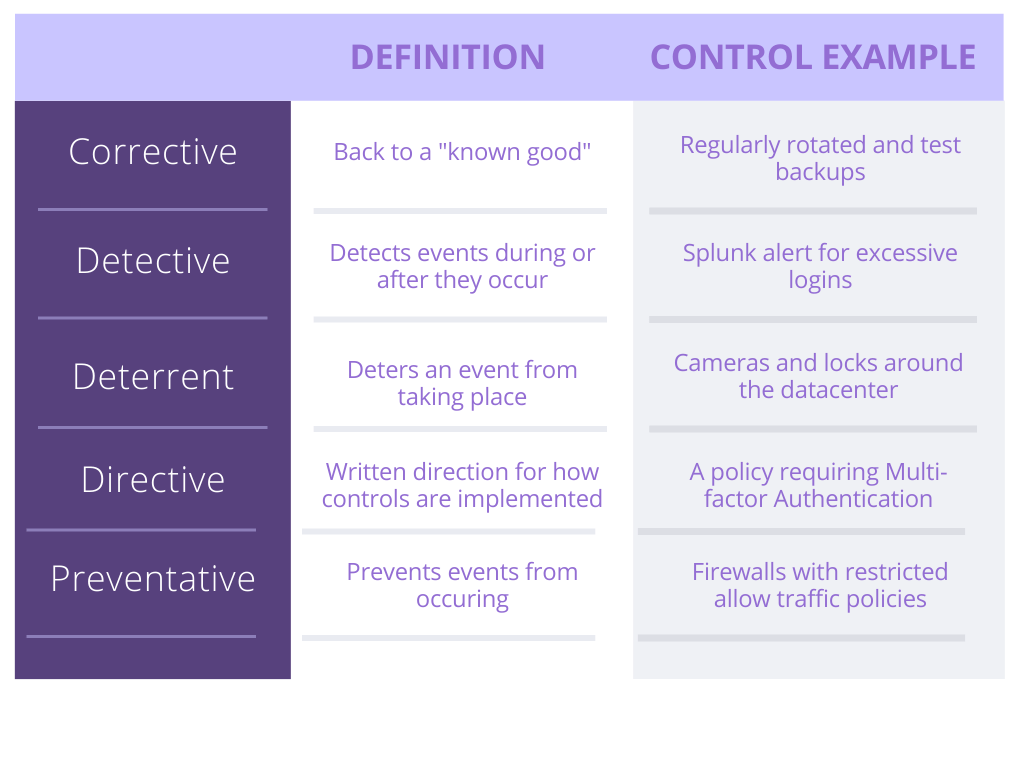
Controls can be categorized into four buckets, namely: administrative, technical, physical, or operational. From there, they can be further broken down by control functionality. A good example of control functionality is in Rogers and Dunkerly’s book: deterrent, preventive, detective, corrective, directive control.
Here are some examples of how these categorizations play out:
We recommend a Control Validation approach with a bottom-up methodology applying a Maturity Matrix to each control identified in the environment. Each control is reviewed Software-Based and Interview-Based Assessments to gather the required information. This information is aggregated based on control functions to provide higher-level insight. By applying assessment information at the lowest state possible, you are able to drill down with high fidelity to identify gaps and understand remediation. The primary goal is to fully understand your current environment before making decisions about new investments.
Please stay tuned for additional blog articles that provide examples of how Concanon analyzes a customer’s investment in security controls to provide the best decision making possible.
Concanon provides Control Validation services to help security leadership understand and communicate their investment in to risk mitigation. We pride our selves on being a data solutions company for data based decision makers. Contact us today for a quick call to see how we can help you solve your issues with Control Validations.
Anthony Giallombardo is the Director of Cyber Security Markets at Concanon. He designs, implements, customizes, and upgrades security solutions for large enterprise environments. He successfully deliveres business innovations, while addressing non-functional drivers such as costs, security, interoperability, scalability, and availability of services. Anthony is responsible for bringing Control Validation and SOAR capabilities to Concanon and delivering them to over 100 customers worldwide.